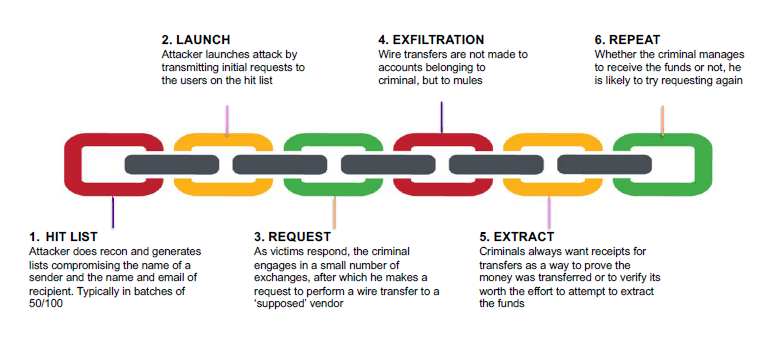
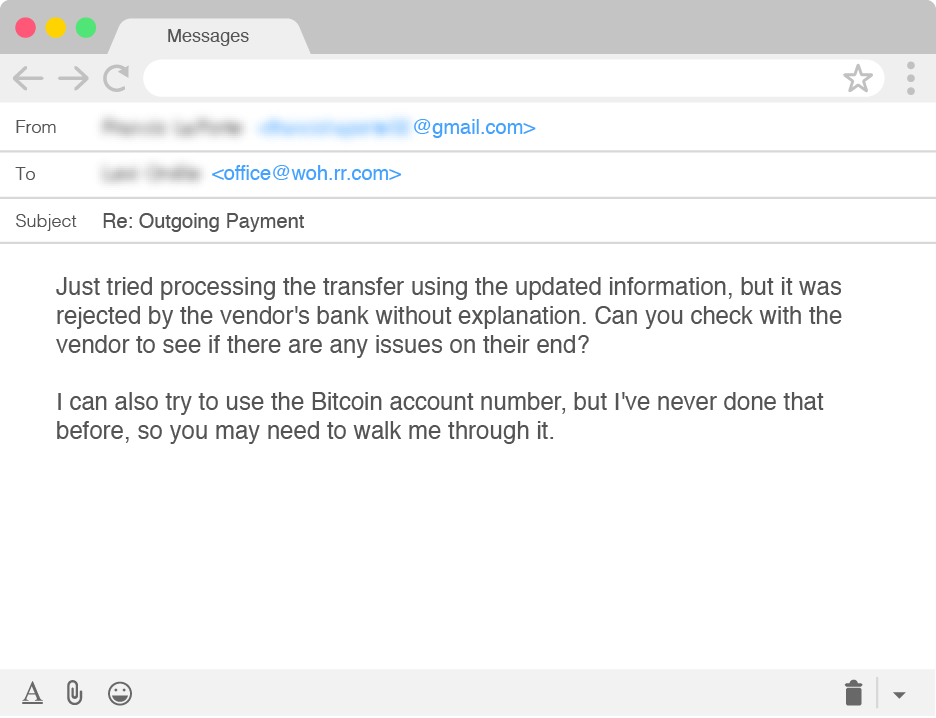
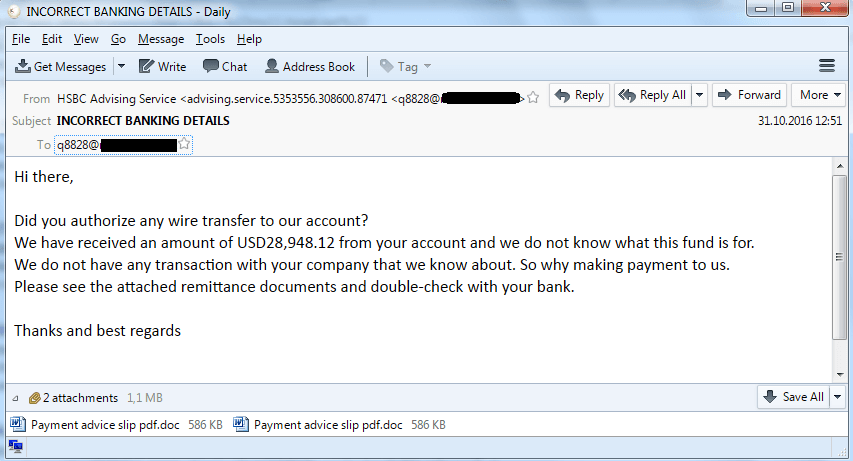
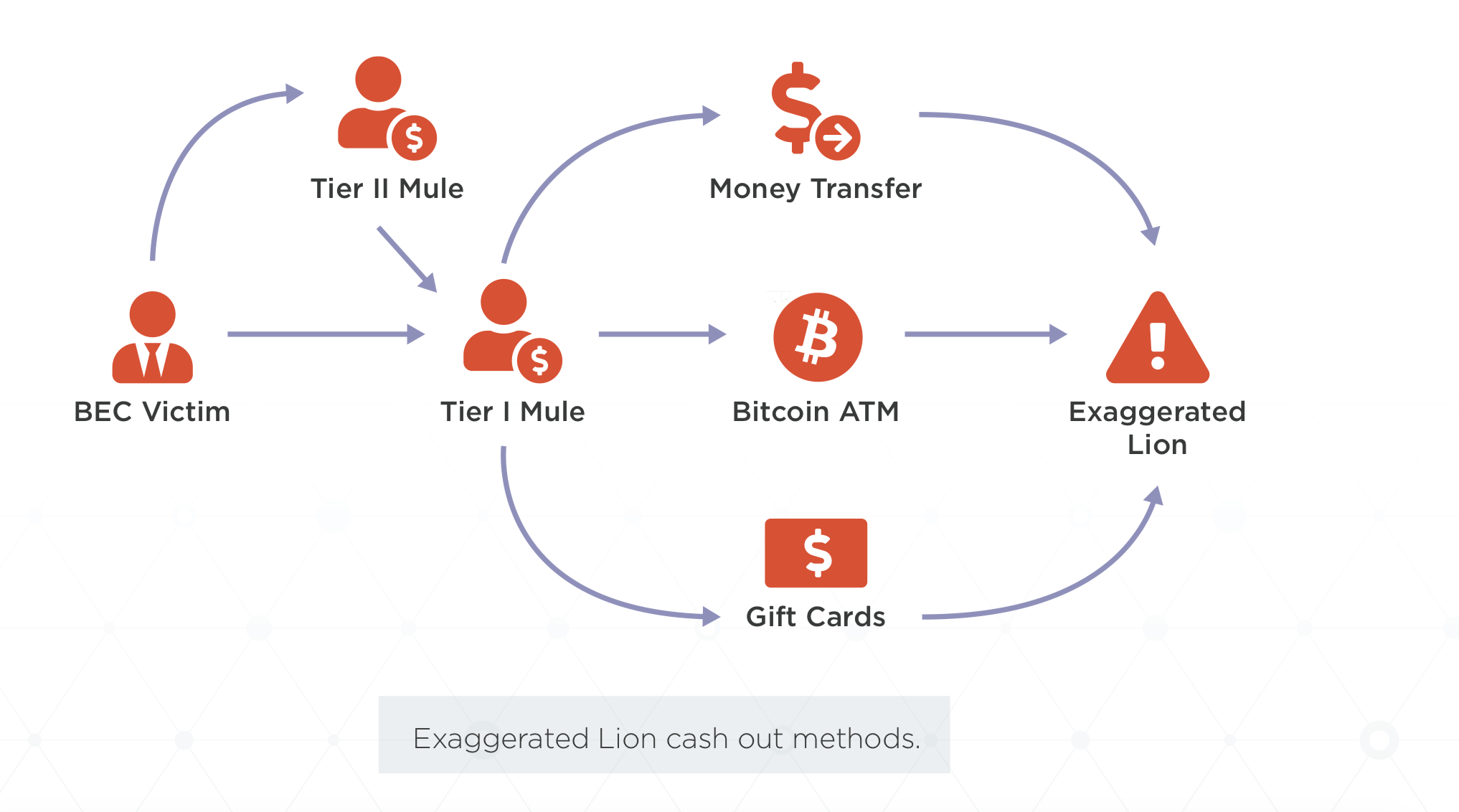
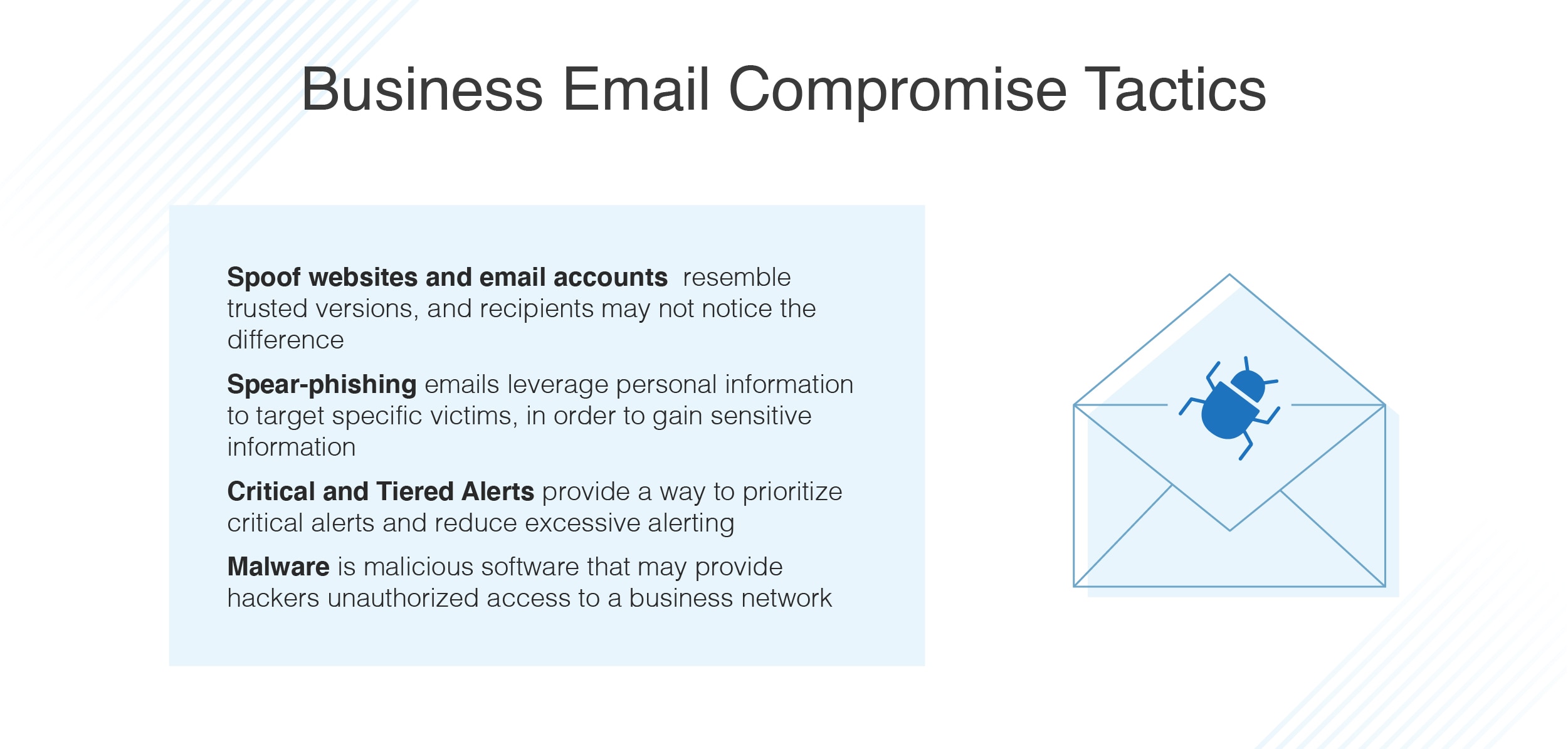
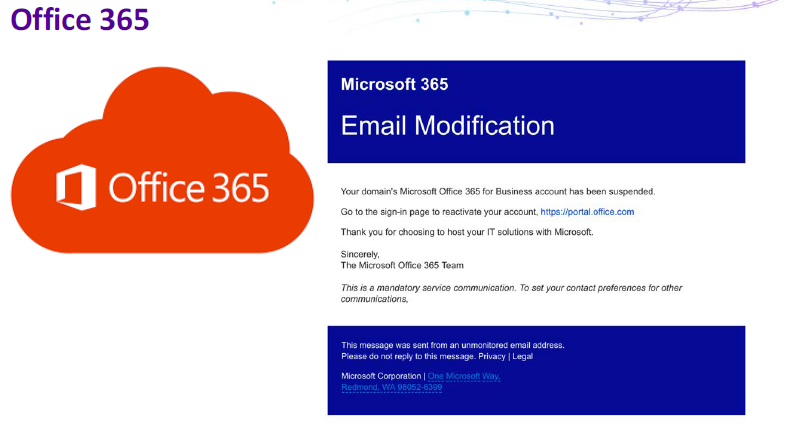
Business Email Compromise (#BEC) Email Forwarding In Action - Malware News - Malware Analysis, News and Indicators

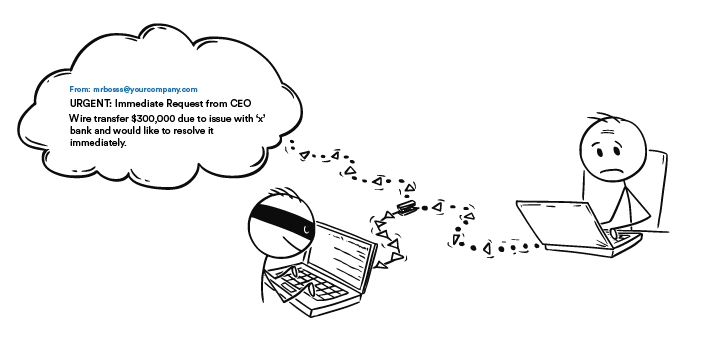
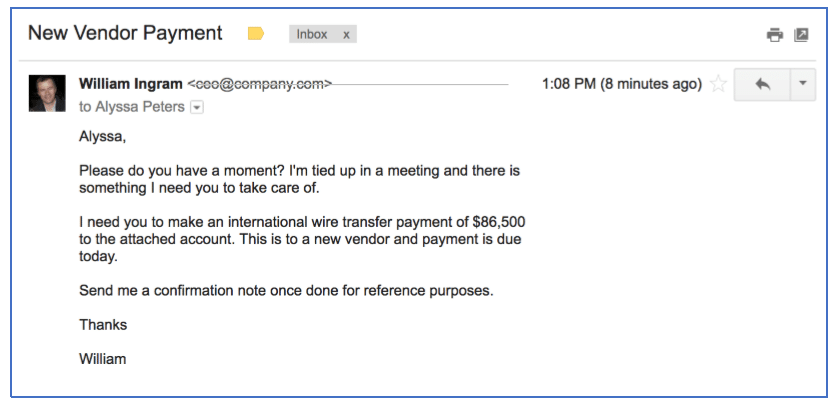
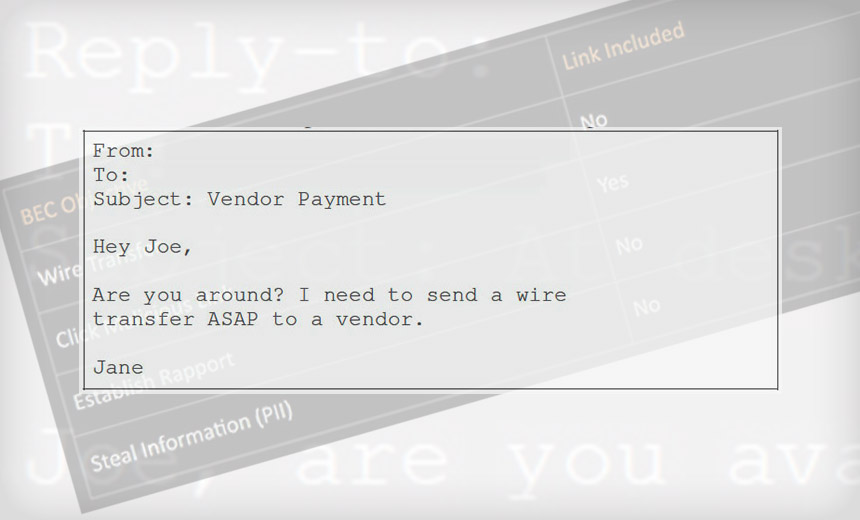
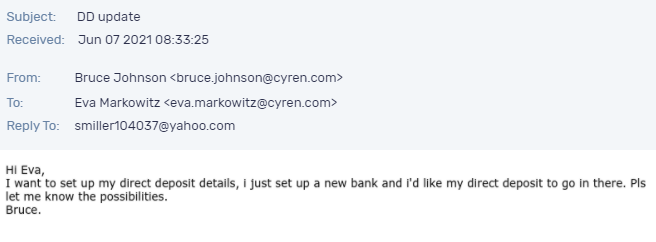
Typical short BEC fraud message, demanding urgency and a wire transfer | Download Scientific Diagram

Typical short BEC fraud message, demanding urgency and a wire transfer | Download Scientific Diagram